picoctf2019-writeup
picoCTF2019 writeup
Project maintained by johantannh Hosted on GitHub Pages — Theme by mattgraham
Glory-of-the-Garden
Points: 50
Problem
This garden contains more than it seems. You can also find the file in You can also find the file in /problems/glory-of-the-garden_6_0d6d3ea97757b84c7a51a38daa7dca8d on the shell server.
Hint
What is a hex editor?
Solution
Solution here
Flag
Flag
unzip
Points: 50
Problem
Can you unzip this file and get the flag?
Hint
put the flag in the format picoCTF{XXXXX}
Solution
Solution here
Flag
Flag
So Meta
Points: 150
Problem
Find the flag in this picture. You can also find the file in /problems/so-meta_1_c8994cc94991979b60e80828d19f75bf.
Hint
What does meta mean in the context of files? Ever hear of metadata?
Solution
Solution here
Flag
Flag
What Lies Within
Points: 150
Problem
Theres something in the building. Can you retrieve the flag?
Hint
There is data encoded somewhere, there might be an online decoder
Solution
Solution here
Flag
Flag
extensions
Points: 150
Problem
This is a really weird text file TXT? Can you find the flag?
Hint
How do operating systems know what kind of file it is? (It’s not just the ending! Make sure to submit the flag as picoCTF{XXXXX}
Solution
Solution here
Flag
Flag
shark-on-wire-1
Points: 150
Problem
We found this packet capture. Recover the flag. You can also find the file in /problems/shark-on-wire-1_0_606ee6b0b78f6987c7b12f43253b2d9b.
Hint
Try using a tool like Wireshark What are streams?
Solution
Use this wireshark filter udp.stream eq 6
Flag
picoCTF{StaT31355_636f6e6e}
WhitePages
Points: 200
Problem
I stopped using YellowPages and moved onto WhitePages… but the page they gave me is all blank!
Hint
Solution
- Use a text editor such as Notepad++ to open the given file
- Replace the unknown characters with 0
- Replace the whitespaces with 1
- Use an online binary to text decoder to decode the resulting binary string to get the flag.
Flag
picoCTF{not_all_spaces_are_created_equal_3bf40b869ee984866e67f3057f006a92}
c0rrupt
Points: 250
Problem
We found this file. Recover the flag. You can also find the file in /problems/c0rrupt_0_1fcad1344c25a122a00721e4af86de13.
Hint
Try fixing the file header
Solution
After examining a PNG image file from the picoCTF website E.g :

The file header can be seen using a hex viewer :
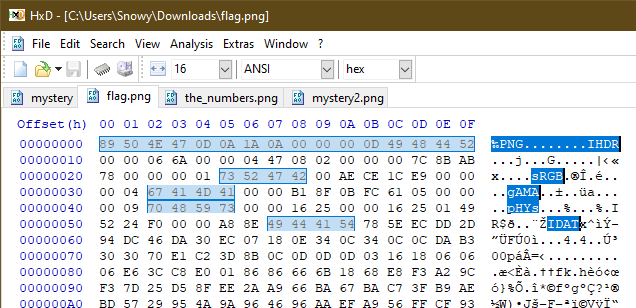
Using the file header as an example, arrange the original file header from this :
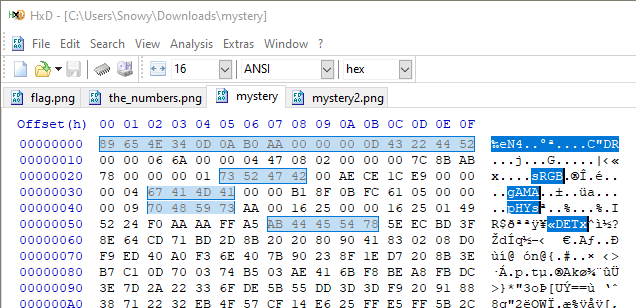
to this format :
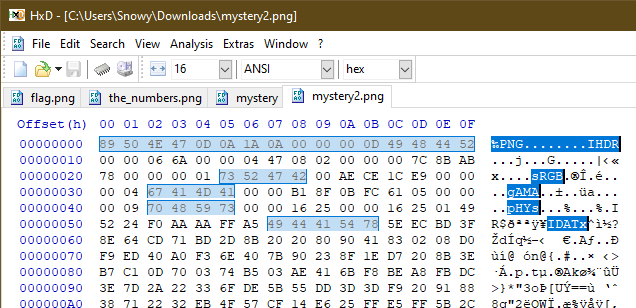
After editing the file header, save in hex editor and a new image will be obtain :

Flag
picoCTF{c0rrupt10n_1847995}
like1000
Points: 250
Problem
This .tar file got tarred alot. Also available at /problems/like1000_0_369bbdba2af17750ddf10cc415672f1c.
Hint
Try and script this, it’ll save you alot of time
Solution
- Inspect the hex value and notice that there are many tar files.
- Each tar file name decreases by 1 value
Use a simple python script to untar the file from 1000 to 0
The script done on python 3.6
import tarfile
for i in range(1000, 0, -1):
tf = tarfile.open(str(i)+".tar")
tf.extractall()
Inside there are
Flag
picoCTF{l0t5_0f_TAR5}
m00nwalk
Points: 250
Problem
Decode this message from the moon. You can also find the file in /problems/m00nwalk_1_727ca48dac5da21d2c11635238649314.
Hint
How did pictures from the moon landing get sent back to Earth? What is the CMU mascot?, that might help select a RX option
Solution
Flag
Flag
shark-on-wire-2
Points: 300
Problem
We found this packet capture. Recover the flag that was pilfered from the network. You can also find the file in /problems/shark-on-wire-2_0_3e92bfbdb2f6d0e25b8d019453fdbf07.
Hint
Solution
- Use wireshark filter
udp.port == 22. Notice it forms a unique value - Use a script to extract all src port, strip the value and convert back to ascii
Flag
picoCTF{p1LLf3r3d_data_v1a_st3g0}
WebNet0
Points: 350
Problem
We found this packet capture and key. Recover the flag. You can also find the file in /problems/webnet0_0_363c0e92cf19b68e5b5c14efb37ed786.
Hint
Try using a tool like Wireshark
How can you decrypt the TLS stream?
Solution
- Use wireshark
- Edit > Preferences > Protocols > SSL
- RSA keys list > Edit
- Fill in
- ip - 128.238.140.23
- port - 443
- protocol - tcp
- file - picopico.key
- The stream will be decrypted. Now just follow the TLSv1.2 stream.
- Pico-Flag header is the answer
Flag
picoCTF{nongshim.shrimp.crackers}
WebNet1
Points: 450
Problem
We found this packet capture and key. Recover the flag. You can also find the file in /problems/webnet1_0_d63b267c607b8fedbae100068e010422.
Hint
Try using a tool like Wireshark
How can you decrypt the TLS stream?
Solution
- Use wireshark
- Edit > Preferences > Protocols > SSL
- RSA keys list > Edit
- Fill in
- ip - 128.237.140.23
- port - 443
- protocol - http
- file - picopico.key
- The stream will be decrypted. You will notice there are some
HTTPprotocols - Filter by
httpprotocol(typehttpin the filter) - Look at packet 41 and 42. Under the packet breakdown(right below the packet window), Right click on
Line based text data: text/html> Export packet bytes > second.html - Open second.html and notice that it is a web page with an image vulture.jpg
- Similarly, filter by
httpand look for theGET vulture.jpgtrailer packet(91). - Right click on
JPEG File Interchange Format> Export packet bytes… > vulture.jpg . You will see the same image as seen in second.html - Right click on the
vulture.jpgon your pc > Properties > details - The
authorsmeta data has the flag.
Alternatively, you can Show packet bytes and view by Hex Dump or ASCII. Metadata of an image is always stored in the file header and that is where information can be hidden.
Flag
picoCTF{honey.roasted.peanuts}